Employee Technology Guide
EMPLOYEE TECHNOLOGY GUIDE
(Click on the topic to navigate to that page)
- How to use this guide
- Campus Technology Support
- Your identity
- PantherMail
- PAWS
- VPN
- Wireless connectivity
- Safe computing
- Passwords
- Operating system updates
- Dealing with threats and safety issues
- Computer use policies
- Panther Card
- Other technologies
How to use this guide
Eastern Illinois University is committed to providing the resources and services necessary to keep its employees on the leading edge of technology. To enhance the working and teaching environment, this guide is a reference for accessing various technology services.
Campus Technology Support
Located on the Second Floor of the Student Services Building in Room 3040 (The PantherCard Office), Campus Technology Support is able to provide assistance with your technology-related questions. You may receive assistance by Live Chat (https://www.eiu.edu/its/helpdesk/livechat/), email (itshelp@eiu.edu), by walking in to Campus Technology Support located on the Second Floor of the Student Services Building - Room 3040, or by calling 217 581-4357. You also may follow us on Twitter, @PantherTechHelp
Staff members will be able to assist you with troubleshooting and how-to questions on a variety of computer, application and connectivity issues related to accessing EIU services. Staff members also have the ability to assist you remotely using an application called Connect @ EIU. This is a very helpful tool and often times allows first-call resolution.
When contacting Campus Technology Support, please have the following information available:
- Name and E-number
- If an employee, the EIU red tag number on your computer
- Location
- Phone number
- Full description of the problem and nature of the error message
Live Chat
Information Technology Services now uses an application called Screen Connect to speed service calls on faculty and staff desktop computers.
Screen Connect allows Help/Service Desk service technicians to remotely access your computer and make needed software fixes, updates, virus cleanups, program repairs, etc., saving time and speeding resolution of your situation. Your machine must have a network connection. You, the user, must grant access to your computer, and you retain control at all times and may terminate the session at will. Screen Connect is Web-based, and no software need be downloaded onto your computer. A Help/Service Desk technician will guide you through the process if you agree to participate in a Screen Connect session.
Your identity
E-number
Your E-number is your essential means of personal identification at Eastern. To protect against identity theft, the university limits the use of Social Security Numbers, substituting a nine-digit proprietary number instead. This number can be found on your Panther Card. Use it to identify yourself in all communication with Campus Technology Support.
NetlD
Every Eastern employee is assigned a NetlD. Your NetlD is the same as your EIU email address, without the “@eiu.edu" suffix.
PantherMail
PantherMail, is the official communication channel for all academic and university notices. You should check your account regularly. It is your responsibility to check your account regularly and ensure there is sufficient free space to receive university communication.
Accessing your PantherMail
The best way to access your PantherMail is via the Web interface (www.eiu.edu.panthermail). Simply log in with your EIU NetID and password in the spaces provided in order to get started.
Official email verification
Phishing scams continue to target university email accounts. Everyone needs to be on the lookout for suspicious emails asking for username and password information. It only takes one or two people to fall victim to a phishing scam to negatively affect the delivery of campus e-mail.
Some quick tips to avoid becoming a phishing victim:
- Never respond to an email asking for password information.
- Check the URL before clicking on odd looking messages to make sure it's really eiu.edu
- Always make sure the URL ends with eiu.edu.
- Eastern will never ask for your password in an email.
- Send suspicious emails to phishing@eiu.edu
Eastern maintains a website that will tell you if a campuswide email you have received is actually from Eastern. If you receive an email purporting to having been sent from the university and you are suspicious about its nature, go to https://www.eiu.edu/panthertech/email_verification.php If the email is listed there, it is safe to open.
PAWS
Find your employee information on PAWS
PAWS (Panther Access to Web Services) is an online application that enables employees to access a variety of information via the Internet. All you need is a computer with access to the Internet and a Web browser.
Through PAWS, users can securely
- „ Look at payroll records and pay stubs
- „ View leave reports and balances
- „ See W-2s and tax data
- „ Pay university bills
- „ See records and transcripts
- „ Obtain your automobile parking pass
From the main EIU home page, click on the PAWS link in the upper right corner.
You will be taken to the following page:

Login to PAWS. You will need your NetID and password:

Laptop security
There are enough threats to contend with when you are working on a workstation on a hard-wired network. When you work wirelessly, with a laptop, there are even more problems to deal with. Chief among them are physical theft and sniffing.
Because a laptop is completely portable, it can easily be lost or stolen. Remember, if you can carry away your laptop, someone else can, too. Never leave your laptop unattended. If you have to leave your office, lock your door or put your laptop in a locked desk. Never leave a laptop in a car.
You should be especially careful not to load sensitive files on a laptop, particularly those containing personal information concerning identity such as names, Social Security Numbers, phone numbers, ages or addresses, or proprietary fiscal information.
VPN
When using a laptop on a wireless network, you run the risk of having your data intercepted. A wireless signal is merely a radio signal, and it can be compromised by persons wishing to steal information or cause harm. You can avoid such threats by connecting through Eastern's AnyConnect Virtual Private Network, or VPN, when working remotely on university business.
Employees can find VPN installation instructions on the ITS software download page, https://www.eiu.edu/its/helpdesk/swdownloads.php on the ITS website.
Now that Cisco AnyConnect is installed, how do you connect next time? (Windows)
- Click Start.
- Select All Programs.
- Select Cisco
- Select Cisco AnyConnect VPN
- From Off Campus select EIU from off campus in the connect to:
- From On Campus select EIU on campus in the connect to:
- Select the Group name you were provided from Network Services.
- Fill in the Username and Password fields with your EIU username (email ID) and password.
- Click Connect.
VPN for Macintosh
For setting up VPN with Mac operating systems, go to this page.
For assistance setting up VPN on iPads, contact Campus Technology Support.
Wireless connectivity
Using the wireless network
The wireless network at Eastern, called “eiuwifi,” allows notebook computers and some handheld devices to connect to the campus network using wireless/radio frequency technology rather than via traditional Ethernet cable.
The advantage of the wireless network is that it allows for mobility. Using a wireless-capable notebook allows you to access the campus network from locations that do not have traditional network connections, such as common areas, lounges and outdoor areas.
When purchasing a notebook computer, make sure you purchase one with an internal wireless card meeting 802.11n (preferred) or 802.11g (acceptable) specifications. Information Technology Services has provided wireless access points throughout every academic building and residence hall common area on campus. These are listed in this guide.
Caution: Wireless not encrypted
Wireless Internet access at Eastern is neither secure nor encrypted. Use of the wireless network for anything other than general Web browsing is not recommended. You should never send sensitive data such as Social Security Numbers over the wireless network.
Wireless authentication procedure for laptops
University faculty and staff must obtain access to the wireless network by logging in with their EIU username and password, just as they do with their desktop machine or to log into their e-mail account. Guests on campus have a similar log-in process.
Benefits to the university include better protection against virus infections, control of illegal peer-to-peer file sharing and greater ability to detect malicious activity on the network.
Users of Eastern's wi-fi network should be aware that the network remains unencrypted, and they should never transmit sensitive data such as personal financial information or Social Security Numbers unless they are logged in to the university's VPN remote desktop application.
Faculty/staff authentication for wireless access:
After you establish a wireless connection and open an Internet browser, you will see this screen. Enter your NetID and password and click submit. Your laptop now will be able to function on the Eastern network. If you don’t have a NetID and password, click the “Register as Guest” button instead:
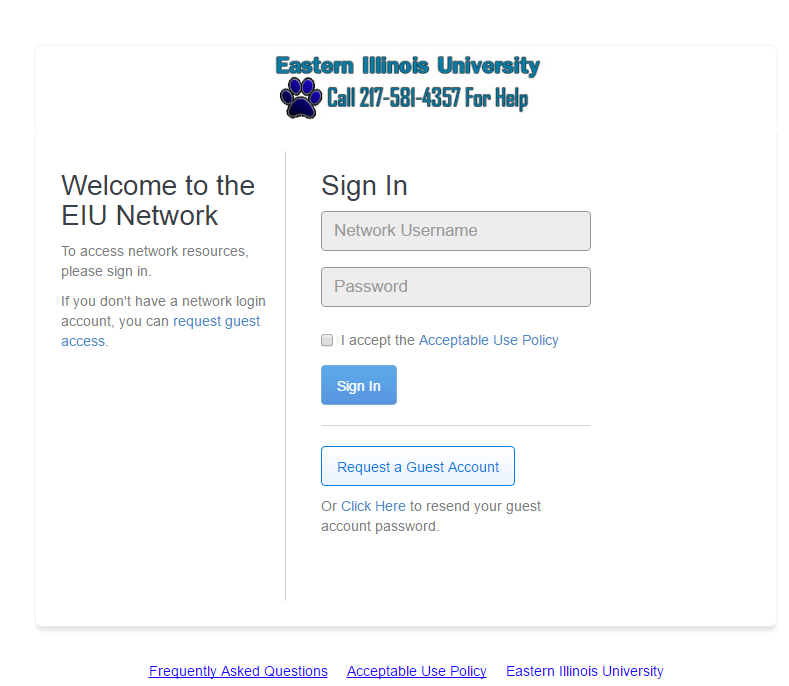
If you click the Register as Guest button, you will see the Network Guest Appropriate Use Policy. Guest users should review the policy, then enter a valid personal e-mail address, first and last names and click submit
If you accidentally click the guest button, then realize that you do have a NetID and password, click “Log in with EIU Account” to return to the standard EIU credentials logon screen.
You will need to review the usage policy if you haven’t yet done so and agree to install the policy key client. This will occur only for machines that do not yet have the policy key client and which are logging on for the first time. If you click “I do not accept,” the client will not be installed and your computer will not have access to the internet.
Once the policy key client is installed, the machine will have wireless internet access.
Faculty and staff who install the policy key client will have 30 days of wireless network access before having to login again.
Guest authentication for wireless access:
Guest users must self-register to get a guest ID and password to be used for all future wireless sessions. The ID and password expire after one week. For example, “Guest Bob” visits campus on a Friday evening, using wireless self registration, installing the policy key client and accessing the wireless network. Later, he shuts down and goes home. He returns Saturday with his same laptop and reconnects to the wireless network. He will then have to self-register again as guest. Assuming he did not uninstall the policy key, he will be granted access. If, for some reason, he did uninstall the application, he will have to reinstall it.
Macintosh anti-virus requirements
Once a month, wireless Apple Macintosh users at Eastern will see the following notice informing them that ITS is bringing Macintosh security requirements up to the level already required for Windows machines. ITS offers a free Sophos AV download for faculty and staff to install.
Wireless availability on campus
All administrative, academic areas and residence halls on campus are covered by a wireless signal. Your reception may vary by location and network traffic loads.
Safe computing
There are a number of steps that you can take to help protect your privacy and ensure the safety of your own computer.
Phishing attacks
Remember: ITS will never ask you for your password via email. If you receive an email asking for your password or other personal information, do not respond, and instead, forward the email to phishing@eiu.edu.
If your email account has been identified as compromised, your account will be locked. Once locked, you will not be able to access most EIU services. To resolve this lockdown, you must call Campus Technology Support at 581-HELP to reset your password and unlock your account.
Identity theft
Identity theft is one of the fastest growing crimes. However, you can take steps to minimize the risk of becoming a victim.
What is identity theft?
Identity theft happens when a criminal steals a victim’s identifying information and uses it to get credit, debit cards, apply for bank loans and even steal money from existing accounts. Most victims find out that they have been taken advantage of when they apply for a loan or when creditors call trying to collect on the debts the criminal racks up.
How does identity theft happen?
Identity theft is fairly easy to commit; all that is needed is a Social Security Number, name, birth date and possibly other identifying information such as an address.
Ways to prevent identity theft
- Password-protect sensitive information with non-dictionary passwords and change the passwords frequently (30 days is recommended).
- Shred documents that contain personal information.
- Do not use Social Security Numbers as a form of identification.
- Don’t give out your Social Security Number.
- Check your credit regularly.
Lock your computer
If you are going to be away from your computer for a while, make sure it is locked. This will require you to re-enter your password before you can use your computer again. To perform this task on PCs with Windows operating systems:
- „On your keyboard, press Ctrl+Alt+Delete at the same time, then click Lock Computer.
- „To unlock your computer: Press Ctrl+Alt+Delete again, then type your password in and click OK.
- An even faster way to lock your computer is through the keyboard shortcut: Windows Key + L.
Reporting a problem
If you suspect that someone has guessed your password and accessed your account, change your password immediately. If you suspect that there is a security breach or flaw in the university system, please notify Campus Technology Support at 581-HELP.
Passwords
You must create a password to use in conjunction with your NetID in order to access your university accounts. You should choose a password that would be difficult for others to guess, keep it secure and change it occasionally. Never share your password; remember, you are responsible for all activities tied to your account.
When creating a password, choose one that is easy for you to remember but hard for others to solve. Password security, however, does not end with picking a strong password. In order to ensure full password security, you must also take steps to protect your password.
- Never share your password with anyone: It is against university policy to do so. This includes family, friends, significant others, computer support personnel and supervisors.
- „Never save your password if prompted by your browser or any other programs.
- Avoid writing your password down.
- Never send your password in email, even if the request looks official: Not only is it against university policy, but such requests are most likely phishing attempts.
Strong password rules:
- „ The first character of your password must be alphabetic.
- „ Your password must be a mix of upper and lower case letters.
- „ Your password must contain at least one number.
- „ Your password must be at least eight characters long.
- „ Your password must contain at least one special character from the following list: ! % * - $ :
- „ Your password may not be longer than 15 characters total.
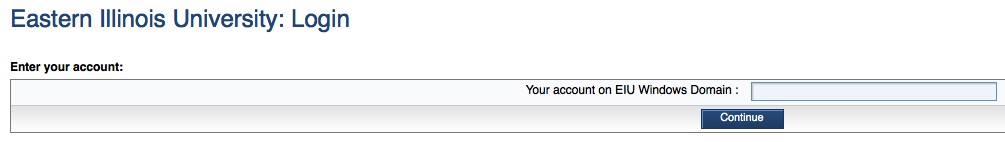
You should change your password regularly. To change your password, go to password.eiu.edu, where you will see the following screen, and follow the instructions there:
Operating system updates for Windows and Mac
One of the most important steps you can take to implement additional security is to keep up to date with current software fixes and service packs. It is recommended that you set the updates to check daily and to automatically download recommended updates and install them.
Updating Windows 7 and 8
Keeping computer operating systems updated is an important step in making sure the computer is secure and continues working at its best. Operating system updates not only fix known security problems but also correct operating problems and sometimes will add new features aimed at making sure users are able to take full advantage of their computer.
Most EIU Windows computers are set to automatically download new updates when they become available. To ensure that your computer receives the latest update, make sure that you restart your computer at least once a week. For example, shutting down over the weekend will help make sure that your computer installs its updates when you come back to work on Monday. To help EIU conserve energy, shut down your computer every night.
However, while Eastern-owned computers should automatically download updates, you can check to make sure your Windows computer is up to date by following these instructions:
Launch Windows Update
To start the Windows Update procedure open Windows Update by clicking on the start menu or start screen, typing in Windows Update and clicking on the Windows Update program.
Once you select Windows Update from either of the options above, Windows Update will open in a new window.
Downloading and installing Windows Updates
Once open, Windows Update will inform you if there are any available updates for your computer.
To begin installing, review the updates that are available and simply click on the Install Updates button.
Once all updates and patches have been installed, the Windows Update window will inform you that the installation was successful and you may be prompted to restart your computer. If this is the case with your updates, save your work and restart you computer as soon as possible. Updates are not applied until the computer restarts.
Alternatively, if your computer installed the updates in the background you may receive a message informing you that updates were installed and your computer needs to restart.
When you restart your computer, Windows will install and configure the pending updates. Make sure that you allow your computer to properly install these updates. Interrupting this process may result in damage to the operating system and/or loss of information.
Updating Apple OS X
Keeping computer operating systems updated is an important step in making sure the computer is secure and continues working at its best. Operating system updates not only fix known security problems but also correct operating problems and sometimes will add new features aimed at making sure users are able to take full advantage of their computer.
Unlike Eastern-owned Windows computers connected to the domain, Apple OS X desk tops and laptops used by faculty and staff do not receive updates automatically. Therefore, it is vital that faculty and staff using Apple OS X computers run Apple's Software Update at least once a month to ensure these computers download and install the latest security patches, operating system updates and Apple software updates.
For information on how to update your Apple OS X desktop or laptop, see the following instructions:
Launching Software Update
To open Software Update, click on the Apple menu (located at the upper left of the screen) and select Software Update.
Once you have selected Software Update from the Apple menu, the Software Update program will open and begin looking for updates available for your Apple OS X computer.
Once all available updates have been found, Software Update will show you a list of all updates that need to be installed.
Downloading and installing Apple OS X Updates
Once you have opened Software Update you will need to select the updates to install. It is recommended that you apply all updates listed. Note that many of the updates may require you to restart your computer. To install the selected items, simply click Install Items.
After clicking on the Install button, Software Update will prompt you to enter your username and password. You must have administrative rights to your computer for Software Update to run properly. If you do not have administrative rights, contact your ISS or the Campus Technology Support for assistance.
Once you have entered your password and agreed to any license agreements required by the selected updates, Software Update will begin downloading and installing the updates.
After all of the selected updates have downloaded and installed, you may be prompted to restart your computer. If this is the case with your updates, save your work and restart your computer as soon as possible. Updates are not applied until after the computer restarts.
Dealing with threats and safety issues
Know the potential threats:
- Hacking: Malicious individuals may exploit the security breaches in your computer software in order to steal your personal information such as passwords and credit card numbers. Hackers may also attempt to secretly install programs on your computer designed to abuse your Internet connection.
- „Malware: Malware is a term used to describe any kind of malicious software that proves detrimental to your computing experience, such as viruses and worms.
- Viruses: Computer viruses are programs that install themselves onto a computer for the purpose of damaging computer files and copying themselves to other computers.
- Worms: Computer worms are typically installed when a user opens an infected e-mail attachment or clicks on an Internet link to an infected Web page. Worms scan electronic address books on your computer for the purpose of sending copies of themselves to other people.
- Adware: Adware programs are installed on your computer for the purpose of displaying advertisements in separate pop-up windows.
- „ Spyware: Spyware programs utilize your machine resources and Internet connection in order to relay information about your Web browsing habits to a parent company.
Solutions
- Sophos: Installing Sophos anti-virus software on your computer will keep it from being infected by computer viruses, worms, adware and spyware. When you install Sophos on your computer, it will be configured to automatically update its malware capturing engine about once a week in order to recognize new computer viruses as they are discovered and reported to Sophos. ITS has made this program available free of charge. A copy can be downloaded at https://www.eiu.edu/its/helpdesk/swdownloads.php
- „Spam filtering: ITS has implemented an e-mail tool on the campus network to filter spam. This application identifies spam e-mail, then tags it as such in the subject line, making the recipient aware of its nature. In addition to tagging spam, this application can filter out threats before they reach your in-box. This program is already running on your campus e-mail account and does not require your intervention.
Web privacy
Eastern uses standard Web server access logs and only gathers information on the time of day, IP address of the accessing Web browser and URL for the purpose of measuring system performance. In compliance with the Illinois State Agency Web Site Act, Eastern websites do not use permanent cookies or any other invasive tracking programs that monitor and track website viewing habits. Eastern websites may, however, use transactional cookies (session variables) that facilitate business transactions. While Eastern uses transactional cookies to track your visit to eiu.edu, and our Web server automatically logs the IP/Internet address of your computer, this information does not identify you personally, and you remain anonymous unless you have otherwise provided personal information.
Although Eastern’s Web pages provide links to other websites, both government and nongovernment, Eastern is not responsible for the privacy practices or the content of such external websites. If you link to another site, you are no longer on a site covered by this privacy notice.
Harassment issues
Do not use university computing facilities to harass anyone. This includes the use of insulting, obscene or suggestive email or postings, tampering with others’ files and invasive access to others’ equipment. Email harassment violates ethical usage of your computer account and may result in university disciplinary action or criminal charges.
Mass mailings and junk e-mail
Never send uninvited email to large numbers of strangers (known as “spam”). In particular, do not send commercial advertisements, surveys, chain mail or questionnaires to anyone who has not given you their permission to do so. Junk e-mail wastes both system resources and the time of those who receive it, and recipients may contact your system administrator with complaints.
Unauthorized use of accounts
Avoid accessing an account not specifically authorized to you, whether that account is on an Information Technology Services system or one at another place. Avoid using an account for a purpose that is not authorized when the account was established, including for personal and commercial use.
Don’t engage in computing activities that are designed to invade the security of accounts. Attempts to decipher passwords, to discover unprotected files or to decode encrypted files are examples.
Proper usage standards require that everyone take prudent and reasonable steps to prevent unauthorized access.
Unauthorized use of software
Do not make unauthorized copies of licensed or copyrighted software. Do not make copyrighted or licensed material accessible from a Web page without the specific written permission of the copyright owner.
Avoid actions that are in violation of the terms or restrictions on the use of software defined in official agreements between the university and other parties.
Examples include the copying of software from personal computers unless it is clearly and specifically identified as public domain software or shareware that may be freely redistributed and the copying of restricted Unix source code.
Enforcement
When instances of improper use come to its attention, Information Technology Services will investigate them. During those investigations, Information Technology Services reserves the right to access private information, including the contents of files and mailboxes, while making every effort to maintain privacy. Those investigations that discover improper use may cause Information Technology Services to:
- „Limit the access of those found using facilities or services improperly.
- „Refer flagrant abuses to deans, department heads, the responsible vice president, the university police or other authorities for appropriate action.
- Disclose private information to other university authorities.
- „Users who violate this policy may have their computing privileges terminated and may be subject to disciplinary action by the university in accordance with appropriate policies or judicial affairs procedures.
Computer use policies
Information Technology Services provides computing facilities and services for the legitimate instructional, research and administrative computing needs of the university. Proper use of those facilities and services supports the legitimate computing activities of Eastern students, faculty and staff. Proper use respects intellectual property rights.
Legitimate instructional computing is work done by an officially registered student, faculty or staff member in direct or indirect support of a recognized course of study. Legitimate research computing is work approved by an authorized official of a university department. Legitimate administrative computing is work performed to carry out official university business.
Intellectual property rights begin with respect for intellectual labor and creativity. They include the right to acknowledgment, the right to privacy and the right to determine the form, manner and terms of publication and distribution.
Proper computing use follows the same standards of common sense and courtesy that govern use of other public facilities. Improper use violates those standards by preventing others from accessing public facilities or by violating their intellectual property rights. Therefore, the basic policy of the university on proper use is:
- Any use of Information Technology Services facilities or services unrelated to legitimate instructional or research computing is improper if it interferes with another's legitimate instructional or research computing.
- „Any use of Information Technology Services facilities or services that violates another person’s intellectual property rights is improper.
- „Any use of Information Technology Services facilities or services that violates any university policy, any local, state or federal law or which is obscene or defamatory is improper.
- „Any use resulting in commercial gain or private profit (other than allowable under university intellectual property policies) is improper.
- „Please refer to our Policies for the complete version of the acceptable use policy.
Panther Card
Your Panther Card is an essential, multi-functional tool necessary for many of your daily activities on campus. Your Panther Card provides the combined functionality of identification and purchasing, all in one card. If you do not yet have a Panther Card, visit the Panther Card office, located in Room 3040 of the Student Service Building.

Lost or stolen cards, chip malfunctionShould your Panther Card be lost or stolen, or your card’s smart chip malfunction, contact the Panther Card office only.
Other technologies
Computer acquisitions
Eastern Illinois University recently updated IGP 103 regarding purchasing computers, servers and software. Regarding general-use computers, it states:
“Information Technology Services (ITS) will establish, publish and maintain the standards for university-purchased computers, and all general-use computer purchases must conform to these standards.”
ITS encourages adopting a Total Cost of Ownership model for purchasing new computers. From the university’s perspective, several costs are incurred with the purchase of a new computer as it moves from the manufacturer to your desk. The total cost of ownership takes into consideration costs such as the hardware, support and setup, warranty service, volume discounts, procurement overhead and purchase time, longevity of the hardware and central management.
By standardizing select models of desktop and notebooks, Eastern will be able to reduce these costs, the time it takes to deliver the computer through setup to user and ITS’s ability to support the device through its years of service. If you need to purchase a computer outside of the recommended models, you may seek approval from the assistant vice president for Information Technology Services or designee.
The Purchasing Department’s computers page provides information on the approved configurations for purchasing desktop, notebook and tablet computers. You will find the standardized models that are recommended. These recommendations are kept up to date by a representative campus committee. To purchase a Windows or Apple computer, follow your departmental purchasing procedure to select an approved configuration and quantity from: https://www.eiu.edu/purchasing/computers.php
Ordering software
Order software at the time your computer is purchased, or later through your department. You can consult with Campus Technology Support to find software that is already licensed and available.
Bookstore discounts
Faculty and staff may take advantage of educational discounts on computers and software at the University Bookstore, located in the Martin Luther King Jr. University Union. Printers, cables, flash drives, security cables and other technology products are also available. See www.eiubookstore.com/ for more information.
Telecommunications
The EIU Telecommunications Office provides all on-campus phone-related services for administrative customers. The office is located in Room 3040 in the Student Services Building (north of MLK Union), for assistance with your on-campus phone services.
LAN drop and faceplate information
Facilities Planning and Management has an installation charge for each new faceplate, so before ordering an installation, be sure there is not an available faceplate behind a bookcase or hidden elsewhere in the room. The following information must be provided:
- Building
- Room number
- Contact person
- Contact's email
- Billing account
Requests are sent to eiumaint@eiu.edu or FPM Work Control at 581-3416.
Have the request approved by the department head. Call the Campus Technology Support at 581- HELP if needed.
Sending computers to surplus
Contact university movers to move computer from user location to the ITS scrubbing area. Go to the Facilities Planning and Management website and fill out an electronic moving taghttps://webappsprod.eiu.edu/eiuwebapps/PROD/PropertyControl/pclogin.php
Units will be updated in inventory, hard drives will be scrubbed, and scrubbed surplus units will be moved to warehouse and then redeployed to new user or sent to CMS in Springfield.
To obtain a surplused computer, contact Property Management 581-7111. You must fill out a moving tag to send a computer to surplus.
Back up your files
Equipment and software can fail. To avoid losing important data and work, you should back up your files. The safest place you can keep critical data files is on a network server.
(Remember, if you back up data on a CD or portable drive, you run the risk of theft or loss.) Not all employees at Eastern have access to network servers, however. Consult your department's instructional support specialist to learn if you have access to network storage. Be particularly careful about backing up sensitive data on portable, plug-in "thumb drives" as these can be easily lost or stolen. If your data is only in one place, it is not backed up.
Follow User Services’ Twitter feed to keep current on service outage announcements and other information: https://www.twitter.com/EIU_ITS
ATAC
The Academic Technology Advisory Committee (ATAC) provides a university-wide forum for discussion of technology issues and the development of recommendations for strategic direction concerning the use of academic communication, computation, information and instructional technologies. The funding is provided by the student Computer Technology Fee and is dispersed by ATAC to provide equipment, software and services for the technology enhanced classrooms and computer labs in order to enhance the learning of the students attending Eastern.
ATAC has subcommittees, ad-hoc committees and task forces as deemed necessary. The standing subcommittees are (1) Academic Technology and Instructional Support, which provides a practical, problem-solving forum for instructional support and technical support staff; (2) Student Technology Fee, which makes prioritized criterion-referenced and standards based recommendations for the use of revenue derived from the computer technology fee; and (3) Coordination of Technology Resources, which reviews the process and makes suggestions for coordinating efforts relative to the selection, purchase, delivery, and installation of technology resources for campus programs and technology initiatives on campus.
ITAC
The primary mission of the Information Technology Advisory Committee at Eastern Illinois University is to provide advice and consultation on information technology to the vice president for Business Affairs as well as serving as a regular advisor to the assistant vice president for ITS.
The committee examines technology issues (both local and global); provides input and reviews strategic plans; recommends priorities for IT initiatives; provides leadership and recommendations regarding enterprise level technology-related matters; provides direction and recommendations for the coordination of technology-related efforts for the university and is a liaison to the EIU community concerning matters relating to information technology.
Academic Technology
- Blackboard Collaborate - Web-based video conferencing system which allows participants to engage in two-way audio, multi-point video, interactive whiteboard, application and desktop sharing, rich media, breakout rooms, and session recording. https://www.eiu.edu/collaborate
- Desire2Learn (D2L) – online learning management system. https://www.eiu.edu/d2l/
- D2L Support – EIU faculty, staff, and students can contact the Center for Online Learning at 217-581-8452 or col@eiu.edu for questions regarding Desire2Learn.
- Global Site Manager - allows users to access web-based tools including OmniUpdate, Menu Manager, Image Manager, Profile Manager and Machforms. https://www.eiu.edu/apps/global/
- Kaltura – online video platform.
- OmniUpdate - Web design software used to create department web pages.https://www.eiu.edu/apps/global/
- Quality Matters - quality assurance for online education through a peer-based approach to continuous improvement in online education and student learning. https://www.eiu.edu/qualitymatters
- Qualtrics - enables users to conduct online data collection and analysis including market research, customer satisfaction and loyalty, product and concept testing, employee evaluations and website feedback. https://www.eiu.edu/qualtrics/
- Turning Point – student response system. https://www.eiu.edu/turningpoint
- Turnitin - detects improperly cited written works and assists both students and faculty in creating authentic and original written works. https://www.eiu.edu/turnitin/
- YouTube - a video-sharing website that allows users to upload content for public and private usage.https://www.youtube.com/user/catsEIU
- Web Office - The Web Office assists with Web-related needs. The office extends its services to all campus departments. Examples of services include new website creation and updating of existing sites, video production for marketing and recruitment purposes, event promotion on eiu.edu, photography, managing the EIU online calendar, Web development: Surveys, forms, etc., email, newsletters and assistance writing/editing Web content. https://www.eiu.edu/web
